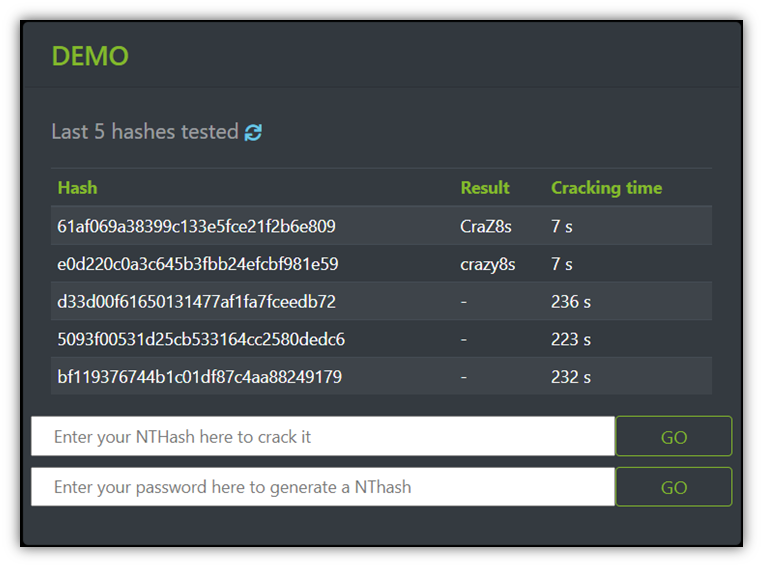
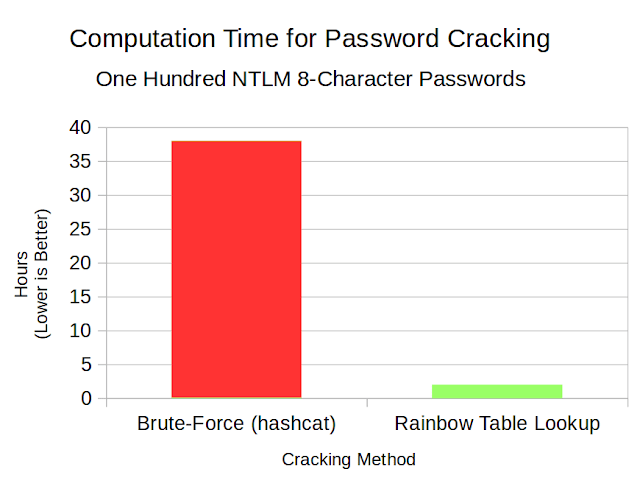
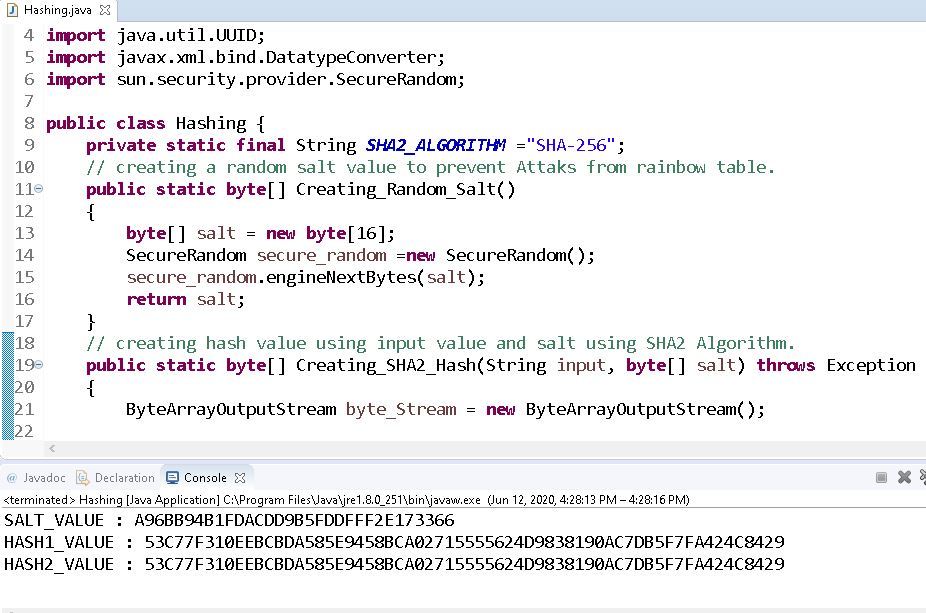
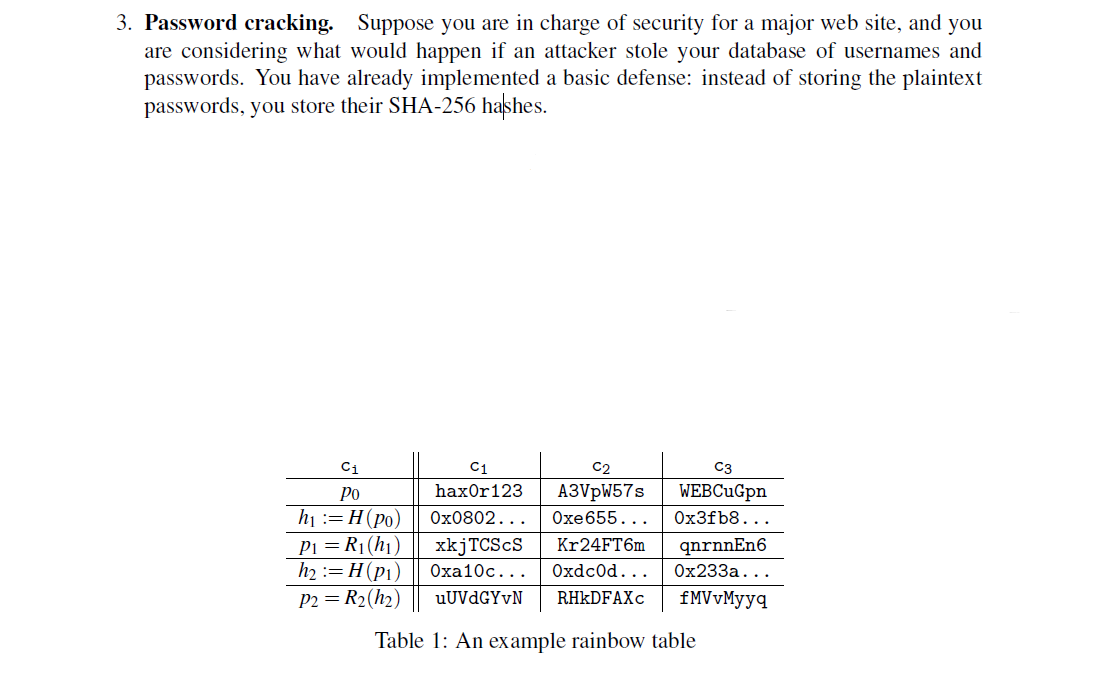
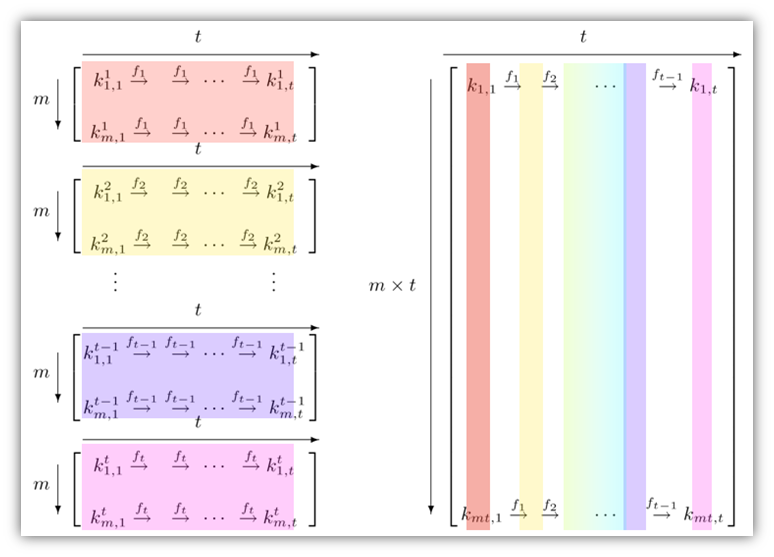
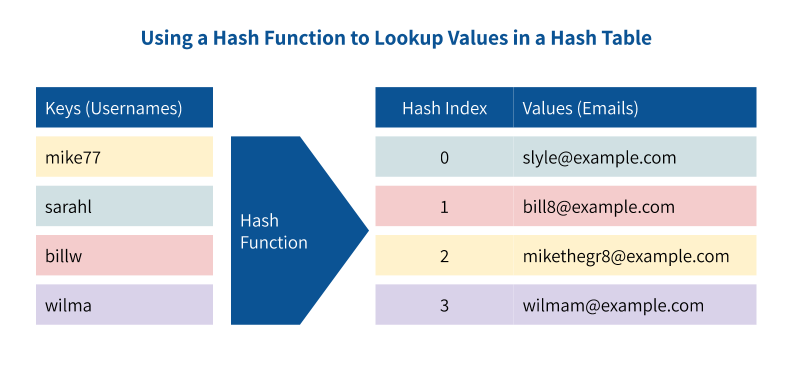
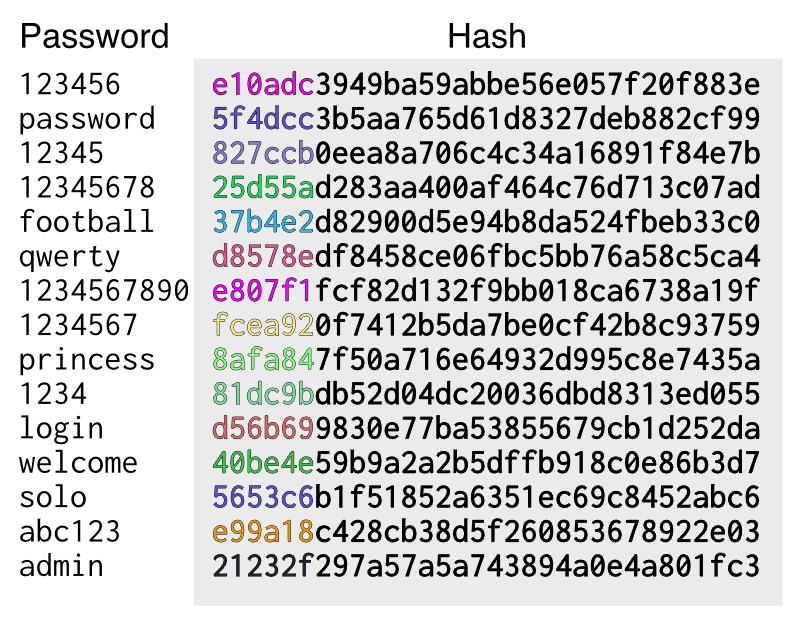
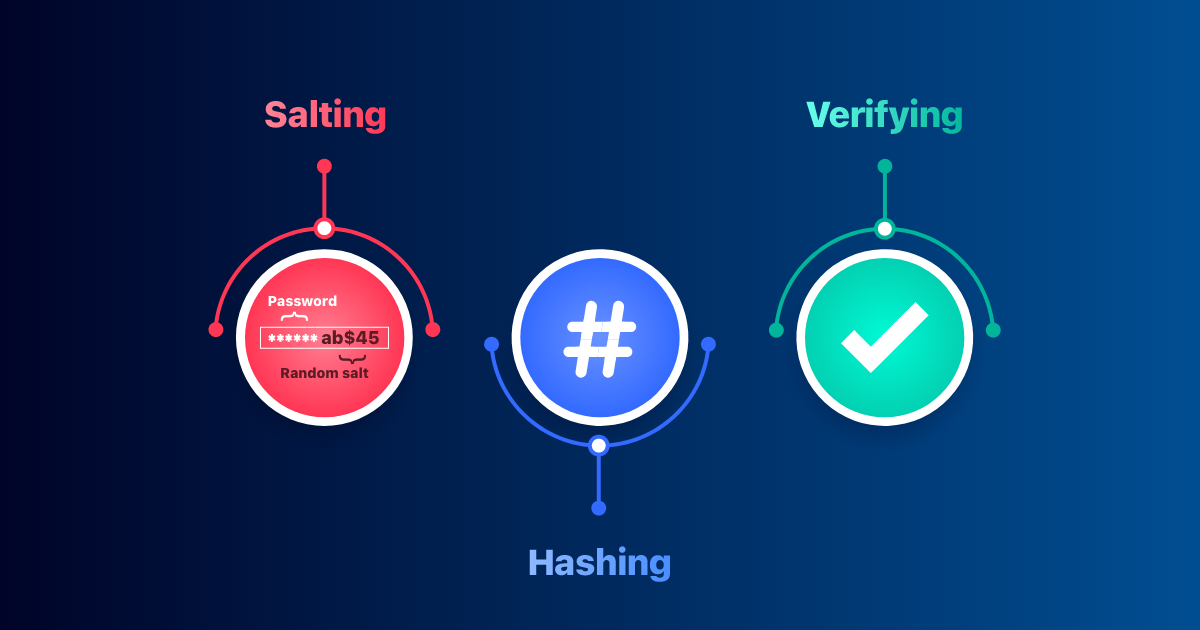
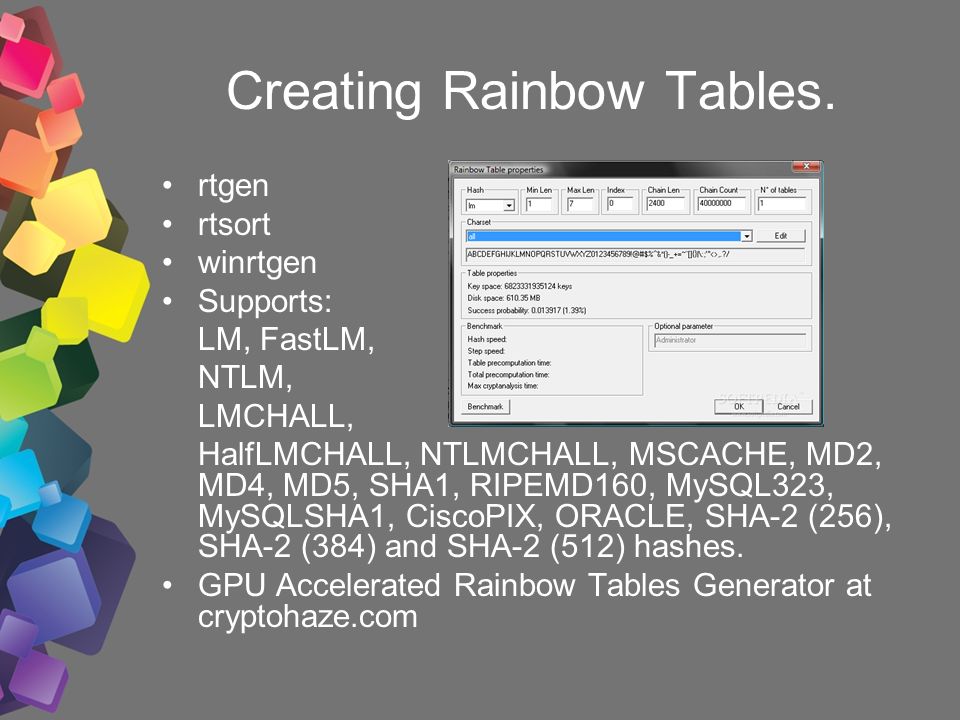
Rainbow table Attack | Password MD5, SHA1, SHA256, Salting | EP18 | Hacking | Cyber security | Tamil - YouTube
SHA-256 Animation' that allows you to intuitively understand the calculation process of the hash function 'SHA-256' with animation - GIGAZINE

KALI – How to crack passwords using Hashcat – The Visual Guide | University of South Wales: Cyber University of the year: Three years running: 2019, 2020, 2021
GitHub - PolyatomicBrian/Make-Rainbow-Table: A simple rainbow table generator supporting MD5, SHA224, SHA256, SHA384, and SHA512, written in Python 2.7.
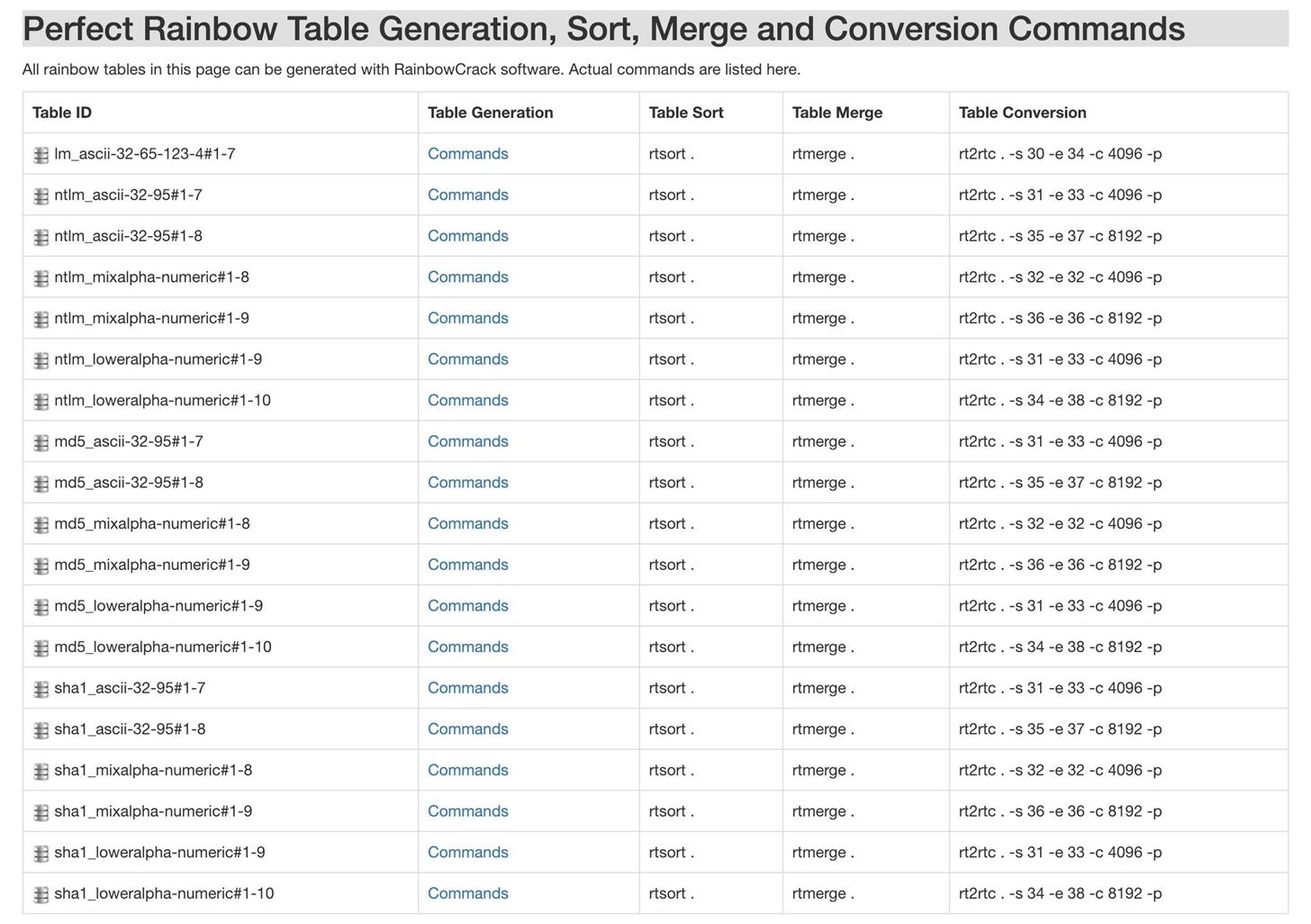
How to Create Rainbow Tables for Hashing Algorithms Like MD5, SHA1 & NTLM « Null Byte :: WonderHowTo