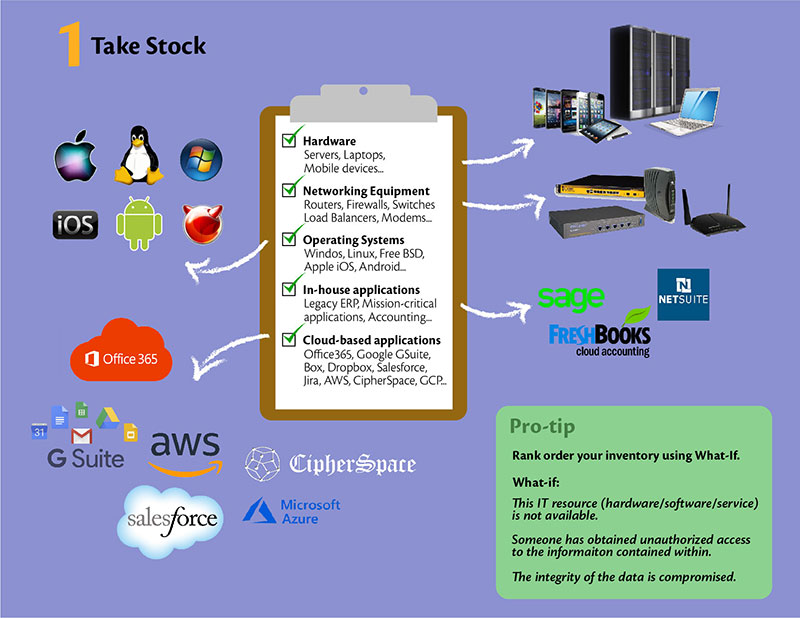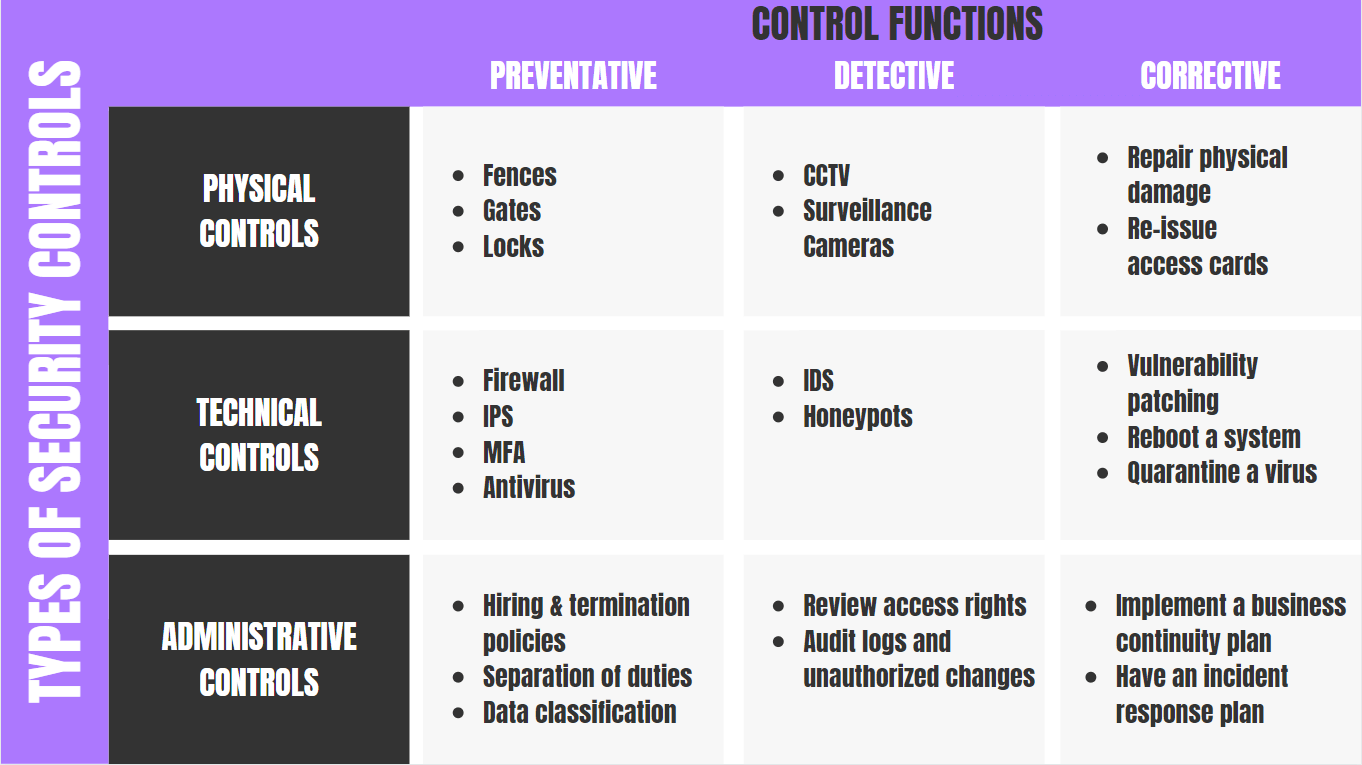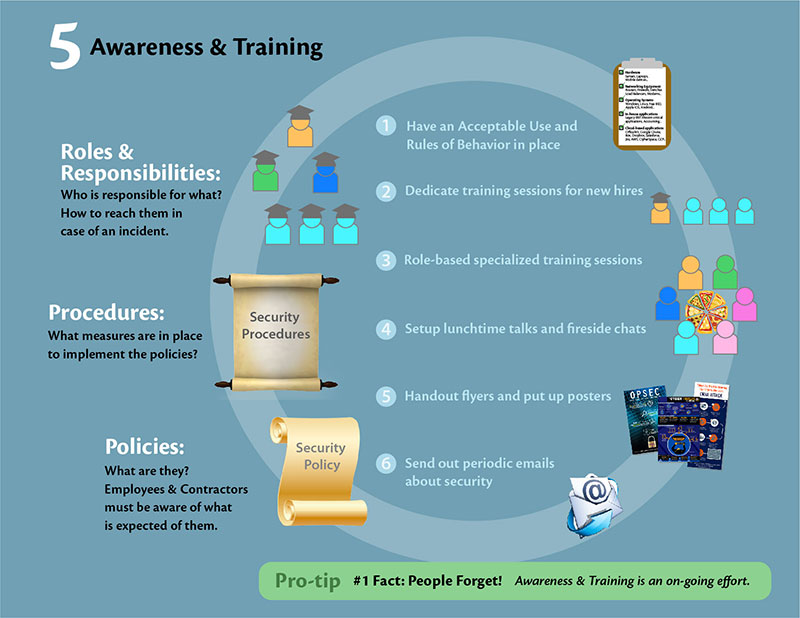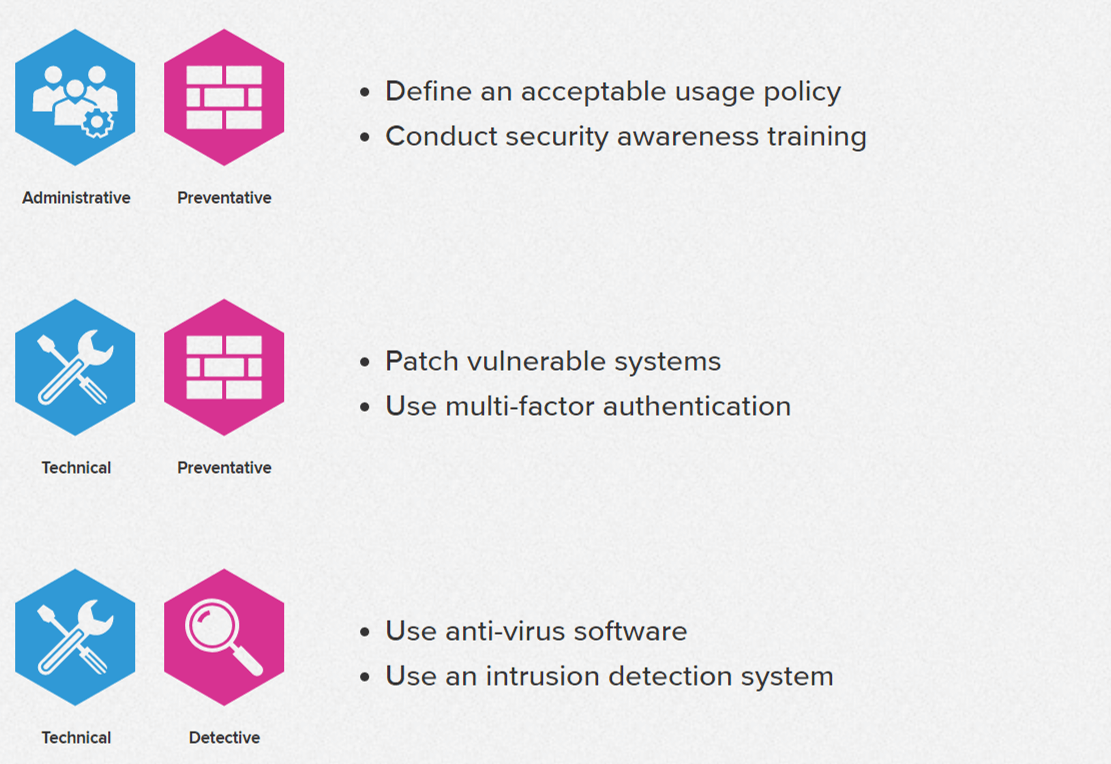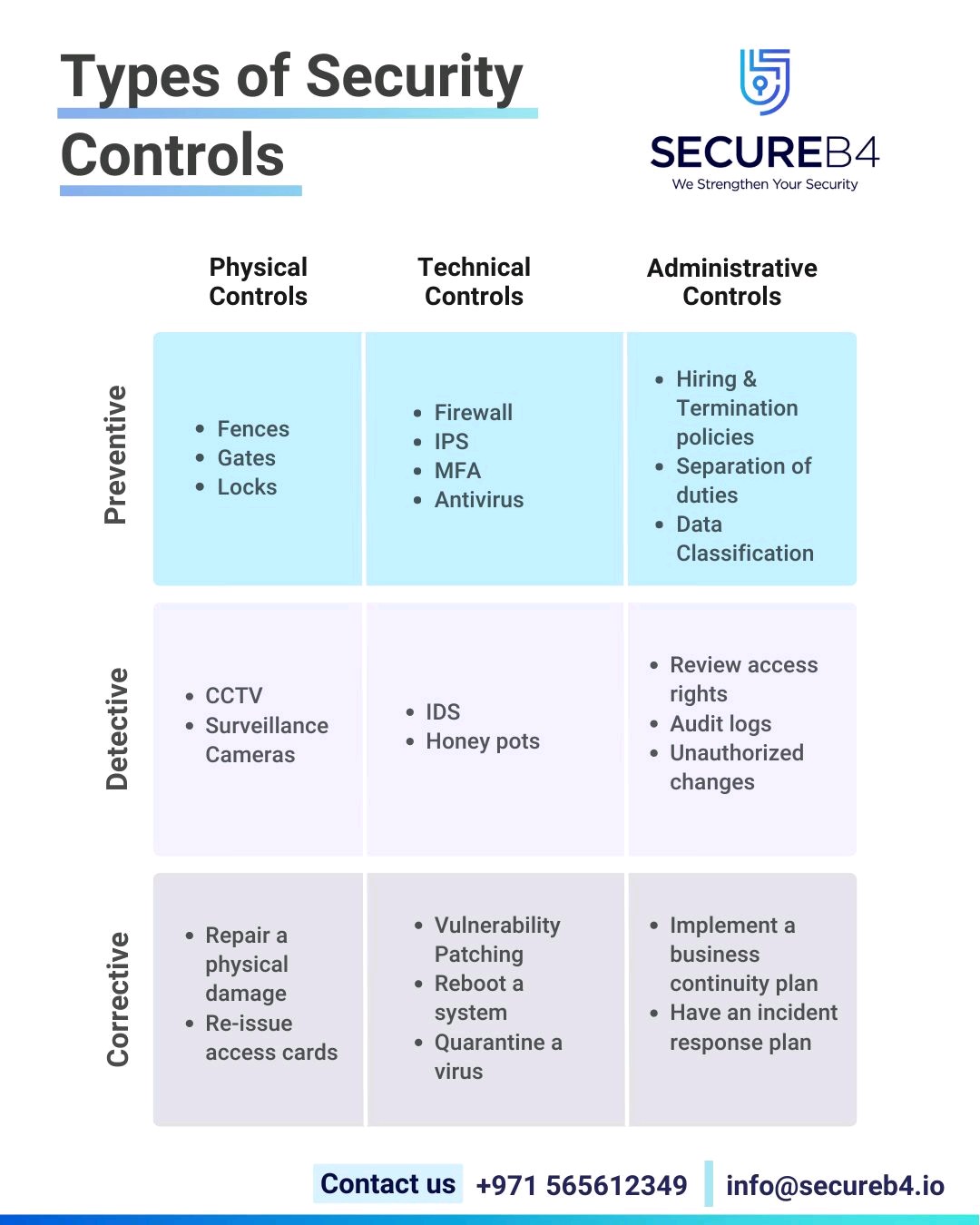
Twitter 上的 Er Suraj Shukla:"Types of Security Controls :- 1) - Corrective 2) - Detective 3) - Preventive 4) - Physical Controls 5) - Technical Controls 6) - Administrative Controls #Linux #infosec #

Controls, Security Controls, and Access Controls? by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu
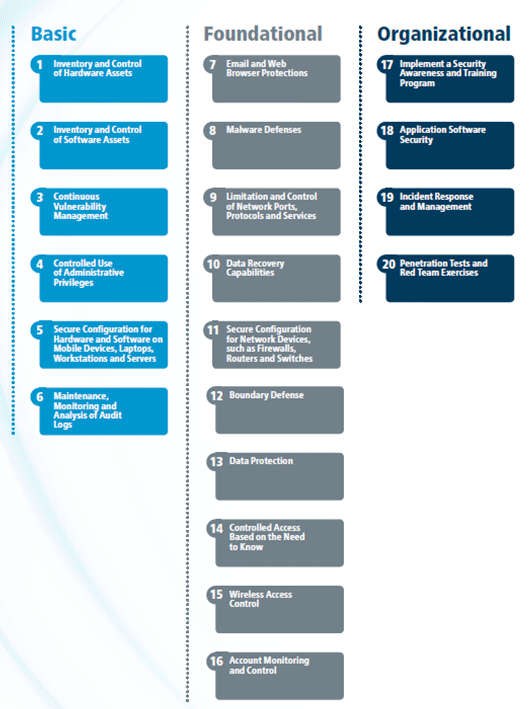
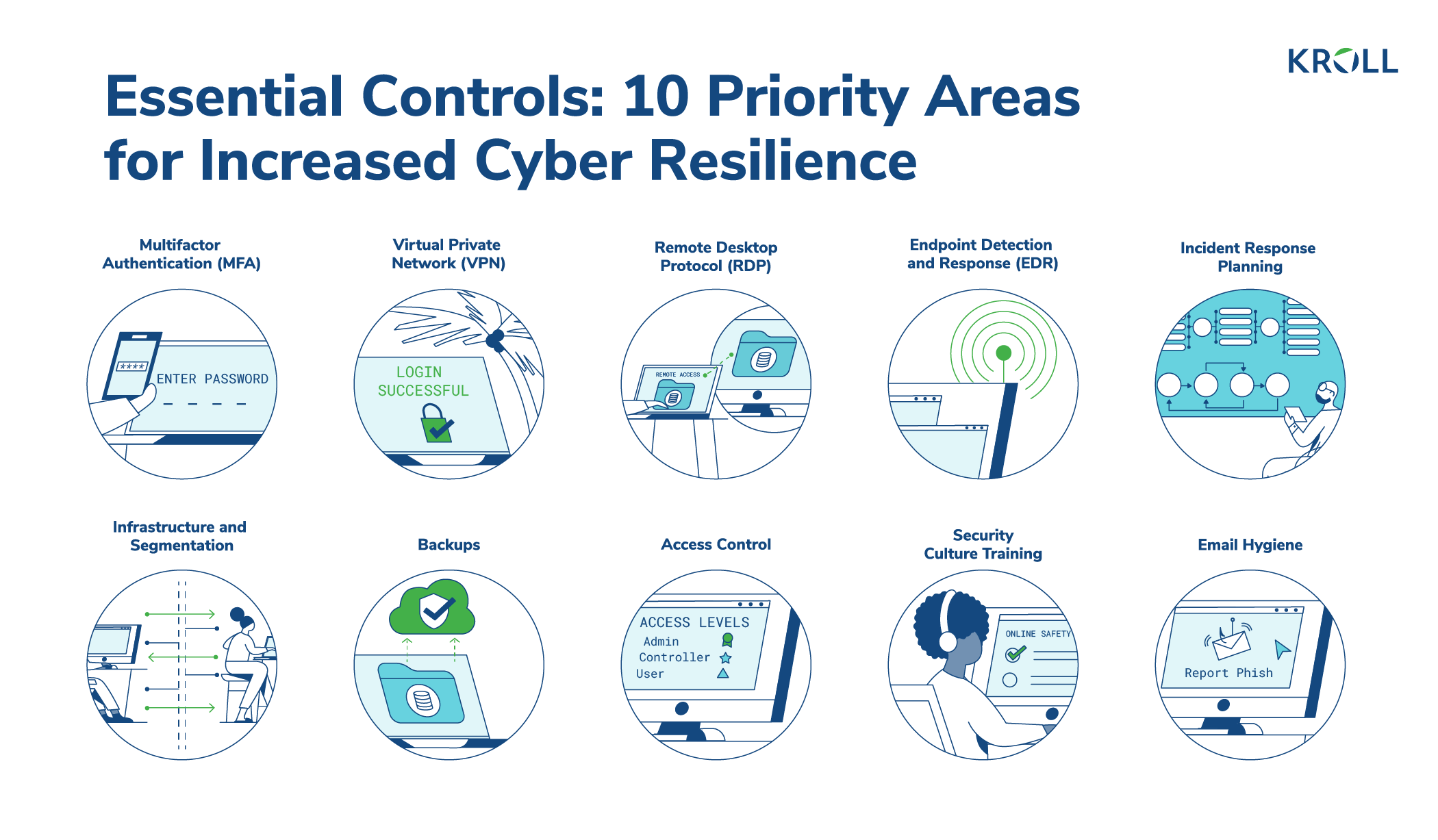
Transportation Management Center Information Technology Security - Chapter 3. Best Practices for Traffic Management Centers Information Technology Security - FHWA Office of Operations

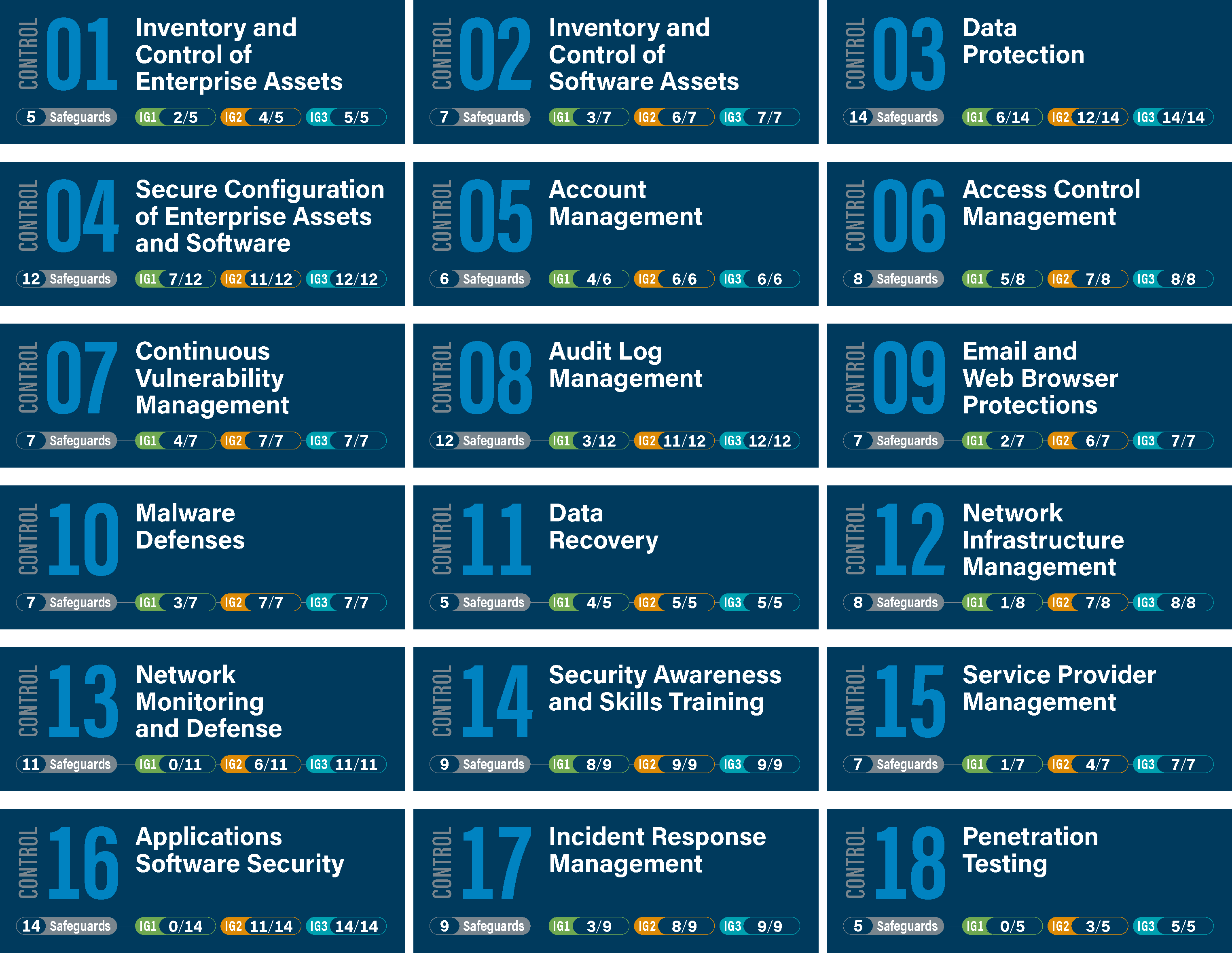
Tabular Presentation Of Security Controls Categorization | Presentation Graphics | Presentation PowerPoint Example | Slide Templates